Embark on an in-depth exploration of routing fundamentals and practical applications with Modules 14 – 16: Routing Concepts and Configuration Exam. This comprehensive guide equips you with a thorough understanding of routing protocols, routing table types, routing metrics, and network path selection.
Prepare to master router configuration, troubleshoot common routing issues, and design secure routing environments.
Through real-world case studies and hands-on exercises, you will gain invaluable insights into the practical implementation of routing solutions. This course empowers you to optimize network performance, enhance reliability, and navigate advanced routing topics such as route summarization and policy-based routing.
Routing Concepts: Modules 14 – 16: Routing Concepts And Configuration Exam
Routing is the process of forwarding data packets across a network from source to destination. It involves determining the best path for the packets to take, based on various metrics such as distance, cost, and reliability.
Routing protocols are responsible for exchanging routing information between routers, enabling them to build and maintain routing tables. Common routing protocols include:
- RIP (Routing Information Protocol): A distance-vector protocol that uses hop count as its metric.
- OSPF (Open Shortest Path First): A link-state protocol that calculates the shortest path to each destination based on link costs.
- BGP (Border Gateway Protocol): An exterior gateway protocol used for routing between autonomous systems.
Routing Table Types
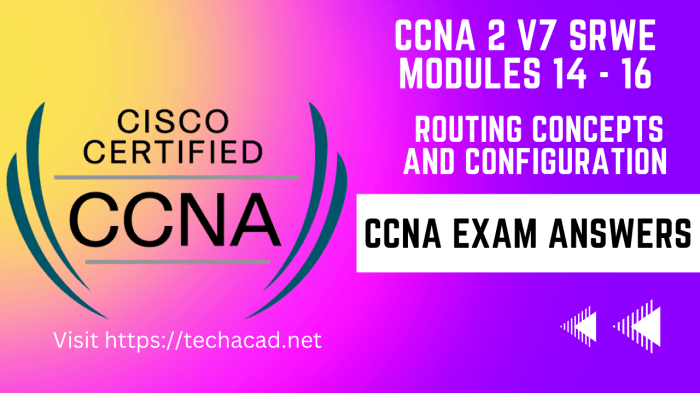
Routing tables contain information about known destinations and the best paths to reach them. There are two main types of routing tables:
- Static routing tables: Manually configured by network administrators.
- Dynamic routing tables: Automatically updated by routing protocols.
Routing Metrics
Routing metrics are used to determine the best path for data packets to take. Common routing metrics include:
- Hop count: The number of hops (routers) a packet must pass through to reach its destination.
- Link cost: The cost assigned to a link based on its bandwidth, delay, and reliability.
- Bandwidth: The maximum data transfer rate of a link.
Routing Topology Design
Routing topology design involves selecting the appropriate routing protocols and configuring them to optimize network performance and reliability. Factors to consider include:
- Network size and complexity
- Traffic patterns
- Redundancy and fault tolerance
Router Configuration
Configuring routers involves setting up routing protocols, creating access lists, and troubleshooting common routing issues.
Static and Dynamic Routing Configuration
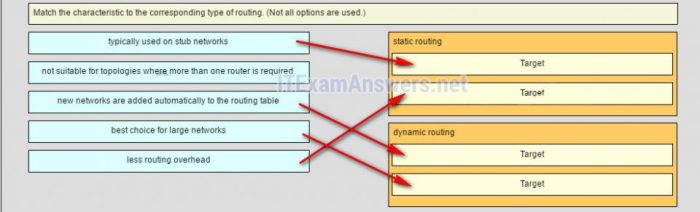
Static routing is configured manually, while dynamic routing is configured using routing protocols. To configure static routing:
- Enter the router’s configuration mode.
- Use the “ip route” command to specify the destination network, subnet mask, and next hop.
To configure dynamic routing:
- Enable the routing protocol on the router.
- Configure the router’s interface with the appropriate network information.
- Verify that the routing protocol is running and exchanging routing information.
Access List Creation and Implementation
Access lists are used to control network traffic. To create an access list:
- Enter the router’s configuration mode.
- Use the “access-list” command to create the access list.
- Specify the access list number, permit or deny action, and source and destination addresses.
To implement an access list:
- Apply the access list to an interface using the “interface” command.
- Specify the direction (inbound or outbound) and the access list number.
Troubleshooting Common Routing Issues
Common routing issues include:
- Routing loops
- Black holes
- Slow or unreliable routing
Troubleshooting steps involve:
- Verifying routing table entries
- Checking interface configurations
- Using troubleshooting commands (e.g., “show ip route”)
Secure Routing Environment Design
Securing routing involves:
- Using strong passwords and encryption
- Implementing access lists to restrict access to routing information
- Monitoring routing activity for suspicious behavior
Network Monitoring for Routing Performance
Network monitoring tools can be used to monitor routing performance. These tools can:
- Track routing table changes
- Detect routing loops
- Monitor link utilization and latency
Routing in Practice

Routing is used in various enterprise network applications:
- Connecting multiple LANs
- Providing access to the internet
- Implementing virtual private networks (VPNs)
Best Practices in Routing Design and Implementation
Best practices include:
- Using a hierarchical routing design
- Implementing redundancy and load balancing
- Monitoring and troubleshooting routing issues
Comparing Routing Solutions
Different routing solutions offer advantages and disadvantages. Factors to consider when comparing solutions include:
- Scalability
- Performance
- Security
Implementation Plan for Routing Solution Deployment
An implementation plan should include:
- Network design and topology
- Routing protocol selection and configuration
- Security measures
- Testing and verification
Evaluating Routing Network Performance and Efficiency
Performance evaluation metrics include:
- Packet delivery ratio
- Latency
- Throughput
Advanced Routing Topics
Route Summarization
Route summarization combines multiple specific routes into a single summary route, reducing routing table size and improving routing efficiency.
Policy-Based Routing, Modules 14 – 16: routing concepts and configuration exam
Policy-based routing allows network administrators to define specific routing rules based on factors such as source address, destination address, or application type.
Redundancy and Load Balancing
Redundancy and load balancing techniques are used to improve network reliability and performance. These techniques include:
- Multiple paths to destinations
- Load balancing algorithms
Routing in Network Virtualization and Cloud Computing
Routing plays a critical role in network virtualization and cloud computing. Virtual routers and software-defined networking (SDN) are used to manage and control routing in virtualized environments.
Routing Security Vulnerabilities and Mitigation
Routing security vulnerabilities include:
- Routing table poisoning
- BGP hijacking
Mitigation measures include:
- Secure routing protocols
- Access control lists
- Monitoring and intrusion detection
Disaster Recovery Plan for Routing Infrastructure
A disaster recovery plan for routing infrastructure should include:
- Backup routing configurations
- Redundant routing equipment
- Procedures for failover and recovery
Essential FAQs
What is the significance of routing in computer networks?
Routing plays a crucial role in computer networks by enabling the efficient and reliable transmission of data packets between devices. It determines the optimal path for data to travel, ensuring that it reaches its intended destination with minimal delay and congestion.
What are the key routing protocols discussed in this course?
This course covers a range of routing protocols, including RIP (Routing Information Protocol), OSPF (Open Shortest Path First), and BGP (Border Gateway Protocol). Each protocol has its own characteristics and is suitable for different network environments.
How does router configuration impact network performance?
Proper router configuration is essential for optimizing network performance and security. This course teaches you how to configure static and dynamic routing protocols, create access lists to control network traffic, and implement security measures to protect against unauthorized access and attacks.